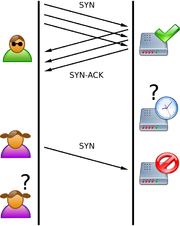
A SYN packet notifies a server of a new connection. The server then allocates some memory in order to handle the incoming connection, sends back an acknowledgement, then waits for the client to complete the connection and start sending data. By spoofing large numbers of SYN requests, an attacker can fill up memory on the server, which will sit their waiting for more data that never will arrive. Once memory has filled up, the server will be unable to accept connections from legitimate clients. This effectively disables the server.
Key point: SYN floods exploit a flaw in the core of the TCP/IP technology itself. There is no complete defense against this attack. There are, however, partial defenses. Servers can be configured to reserve more memory and decrease the amount of time they wait for connections to complete. Likewise, routers and firewalls can filter out some of the spoofed SYN packets. Finally, there are techniques (such as "SYN cookies") that can play tricks with the protocol in order to help distinguish good SYNs from bad ones.
The CERT advisory on SYN Flooding includes an up-to-date list of the vendors who have patches for this attack. All server systems are vulnerable unless patched if traffic from the Internet (or any hostile network) are permitted.
Key point: SYN floods exploit a flaw in the core of the TCP/IP technology itself. There is no complete defense against this attack. There are, however, partial defenses. Servers can be configured to reserve more memory and decrease the amount of time they wait for connections to complete. Likewise, routers and firewalls can filter out some of the spoofed SYN packets. Finally, there are techniques (such as "SYN cookies") that can play tricks with the protocol in order to help distinguish good SYNs from bad ones.

SYN Flood. The attacker sends several packets but does not send the "ACK" back to the server. The connections are hence half-opened and consuming server resources. Alice, a legitimate user, tries to connect but the server refuses to open a connection resulting in a denial of service.
The CERT advisory on SYN Flooding includes an up-to-date list of the vendors who have patches for this attack. All server systems are vulnerable unless patched if traffic from the Internet (or any hostile network) are permitted.

No comments:
Post a Comment